Stop reacting, start protecting: Your data deserves zero-trust security

As Field CTO for Managed File Transfer (MFT) at Redwood Software, I’ve dedicated my career to helping organizations securely move their most critical data. File transfers play a key role in daily operations, but they’ve also become a significant target for cyberattacks.
With years of experience in MFT, I want to share how a proactive, zero-trust security model can help businesses stay ahead of threats and protect what matters most.
The growing risk: Why file transfers are under attack
A single data breach can cost millions, disrupt operations and erode customer trust. File transfers, designed to enable seamless data exchange, are increasingly targeted by cybercriminals.
The question is: Are you reacting to breaches or proactively preventing them?
Recent high-profile cybersecurity incidents show just how vulnerable MFT systems can be. One file transfer provider’s 2024 zero-day vulnerability exposed sensitive data and disrupted business operations for numerous organizations. A more high-profile incident in 2023 resulted in widespread data exfiltration and significant financial losses. Over 60 million customers were impacted. Yet another exploit compromised sensitive data and eroded customer trust for organizations relying on this widely used solution.
Forrester research shows just how much a major security incident matters: Up to 33% of adults would stop doing business with an organization permanently if they found out about a breach that exposed customer data.
Breaches and their impact on business relationships highlight one undeniable truth: Traditional security measures are no longer enough. A zero-trust approach to file transfers is essential for staying ahead of today’s cyber threats.
What is zero trust?
Zero trust is built on a simple principle: “Never trust; always verify.” It assumes that every user, device, or application — inside or outside the network — poses a potential risk. Instead of reacting to threats, a zero-trust approach focuses on proactive protection by continuously verifying access and activity.
Core principles of zero trust
- Verify explicitly: Authenticate and authorize every access request.
- Least-privilege access: Minimize permissions to reduce attack surfaces.
- Assume breach: Design with the expectation of compromise.
- Encryption everywhere: Protect data at rest and in transit.
- Continuous monitoring: Detect and respond in real time.
Applied to MFT, zero trust transforms security from a reactive defense to an active safeguard.
How to build a zero-trust strategy for file transfers
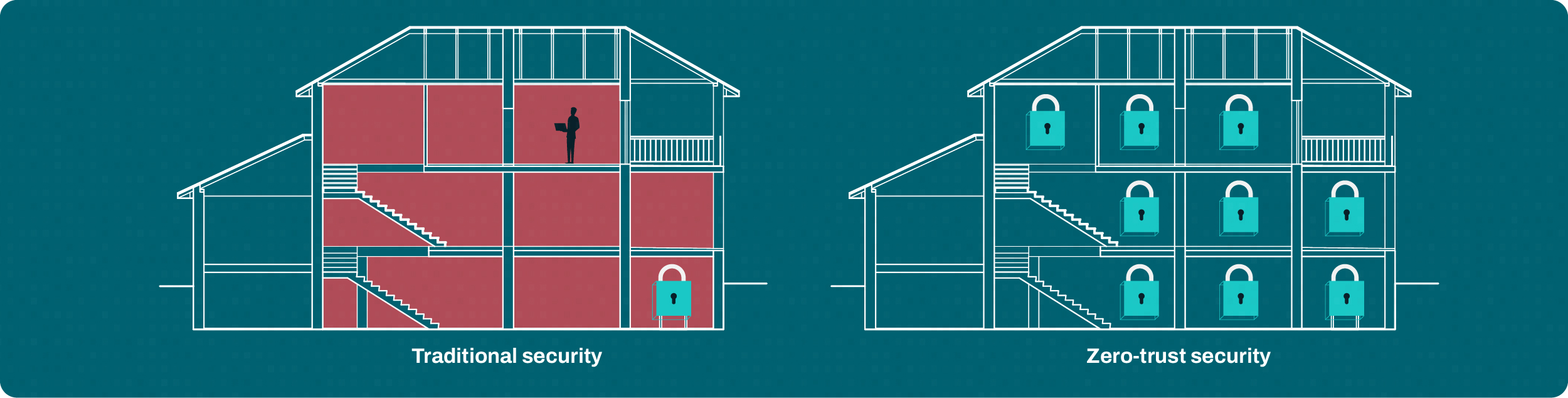
Imagine your business data is like your home. Traditional security is like locking your front door: Once someone’s inside, they can access everything. With zero trust, you have a security guard at the entrance to every room who checks ID before permitting entry.
If you wouldn’t take unnecessary risks with your home and family, why would you do so with your business and customers?
Here’s how you can adopt zero-trust principles for your file transfer environments starting today:
- Encrypt file transfers and data at rest: Secure data in transit with protocols like SFTP, FTPS, HTTPS and AFTP. Use AES-256 encryption for data at rest and PGP for additional layers of protection.
Actionable step: Enable encryption end to end and at rest within two months to reduce risks of data interception or unauthorized access. - Enforce multi-factor authentication (MFA): MFA adds a critical layer of protection by requiring multiple forms of authentication before granting access.
Actionable step: Deploy MFA across all file transfer systems within the next quarter to prevent unauthorized logins. - Implement role-based access control (RBAC): Limit user access to only the files, workflows and systems necessary for their roles.
Actionable step: Review and refine RBAC policies within the next month to verify you’re aligned with the principle of least privilege. - Isolate critical systems with a DMZ gateway: Separate external-facing file transfers from internal networks to prevent lateral movement during a breach.
Actionable step: Implement a DMZ gateway and micro-segmentation within three months for additional layers of isolation. - Enable continuous monitoring and automated threat response: Use tools like SIEM systems to monitor activity in real-time, integrate data loss prevention (DLP) to scan files and automate responses to potential threats.
Actionable step: Evaluate and deploy monitoring tools and DLP solutions within six months to strengthen detection and response capabilities.
Leveraging cloud-native security to uphold zero trust
Cloud security has matured significantly, offering robust features that complement zero-trust strategies. As organizations transition to the cloud, understanding the shared responsibility model is crucial.
Cloud providers secure the infrastructure, while customers are responsible for protecting their data and workflow configurations. It’s important to bridge this gap because misconfigurations, inadequate access controls and integration challenges can leave sensitive data vulnerable. This underscores the need to choose a solution to enhance cloud-native capabilities with advanced MFT security features.
Beyond cloud-native capabilities
While cloud-native security features are essential, many organizations require flexibility and advanced capabilities beyond what traditional cloud file transfer solutions (like AWS Transfer Family) provide.
To avoid vendor lock-in, find an MFT platform that supports multi-cloud environments (AWS, Azure, Google Cloud) and gives you the freedom to transfer data seamlessly across platforms without being tied to a single provider.
Key features of JSCAPE by Redwood’s cloud-native zero-trust approach
- Server-side encryption: Secure data at rest using cloud-managed or customer-managed keys.
- Cloud key management service (KMS): Simplify encryption key handling to meet organizational requirements.
- Object locking and versioning: Prevent accidental deletion or overwriting of critical data while ensuring compliance.
- Auditing and logs: Generate immutable records of file transfer activities for compliance and forensic purposes.
JSCAPE integrates seamlessly with cloud-native security features, offering the zero-trust architecture you need to maintain a strong, future-proof security posture.
If you have hybrid use cases, you’ll need a solution that enables secure file transfers across hybrid environments, integrating on-premises systems with cloud storage. For example, you might synchronize files between an on-premises system and AWS S3 or Azure Blob Storage using a secure MFT agent.
The flexibility to deploy your MFT solution on-premises, in the cloud or in a container will allow you to choose the environment that best meets your compliance, scalability and operational needs.
Choose a true partner for zero-trust implementation
Threats to file transfer systems are evolving. Therefore, your solutions must evolve.
JSCAPE’s zero-trust alignment, hybrid capabilities and deployment flexibility make it the ideal choice for modern file transfer security. Its key capabilities include:
- DMZ gateway: A secure buffer zone that eliminates inbound firewall rules and reduces attack surfaces
- Granular access controls: Fine-grained permissions to protect sensitive data
- Cloud integration: Support for secure file transfers across AWS, Azure and Google Cloud
- Automated workflows: Consistent security policies with event-based automation
Stop reacting to breaches — start preventing them. Learn more about JSCAPE and how to build a proactive security strategy for protecting the data your customers and partners trust you with.
About The Author

Ryan Wood
Ryan Wood is Redwood’s Field CTO for managed file transfer (MFT). With over 17 years in the global B2B integration MFT market, Ryan is a product strategy, roadmapping and execution expert who has held various roles, from Support Engineer to Product Manager. In his 16-year tenure at IBM, Ryan did everything from providing technical support to conducting market research and overseeing the entire product lifecycle.
His diverse experience has made Ryan an adaptable leader, capable of balancing and communicating vision and strategy. He is leading the charge in establishing JSCAPE by Redwood as an industry-leading solution, working closely with Product and Engineering teams to ensure it delivers the business value customers expect and deserve.